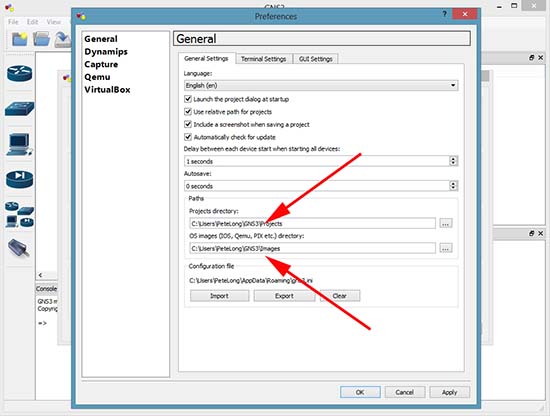
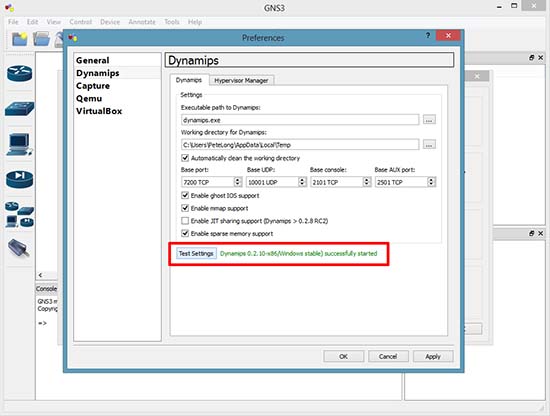
There are literally thousands of commands and sub-commands available to configure a Cisco security appliance. As you gain knowledge of the appliance, you will use more and more of the commands. Initially, however, there are just a few commands required to configure basic functionality on the appliance. Basic functionality is defined as allowing inside hosts to access outside hosts, but not allowing outside hosts to access the inside hosts. Additionally, management must be allowed from at least one inside host. To enable basic functionality, there are eight basic commands (these commands are based on software version 8.3(1) or greater).
- interface
- nameif
- security-level
- ip address
- switchport access
- object network
- nat
- route
Sample Network Diagram
![Cisco ASA Configuration Basic Diagram]()
interface
The interface command identifies either the hardware interface or the Switch Virtual Interface (VLAN interface) that will be configured. Once in interface configuration mode, you can assign physical interfaces to switchports and enable them (turn them on) or you can assign names and security levels to VLAN interfaces.
nameif
The nameif command gives the interface a name and assigns a security level. Typical names are outside, inside, or DMZ.
![basic eight int nameif sec level ip add]()
security-level
Security levels are numeric values, ranging from 0 to 100, used by the appliance to control traffic flow. Traffic is permitted to flow from interfaces with higher security levels to interfaces with lower security levels, but not the other way. Access-lists must be used to permit traffic to flow from lower security levels to higher security levels. The default security level for an outside interface is 0. For an inside interface, the default security level is 100. In the following sample configuration, the interface command is first used to name the inside and outside VLAN interfaces, then the DMZ interface is named and a security level of 50 is assigned to it.
ciscoasa(config)# interface vlan1
ciscoasa(config-if)# nameif inside
INFO: Security level for “inside” set to 100 by default.
ciscoasa(config-if)# interface vlan2
ciscoasa(config-if)# nameif outside
INFO: Security level for “outside” set to 0 by default.
ciscoasa(config-if)# interface vlan3
ciscoasa(config-if)# nameif dmz
ciscoasa(config-if)# security-level 50
ip address
The ip address command assigns an IP address to a VLAN interface either statically or by making it a DHCP client. With modern versions of security appliance software, it is not necessary to explicitly configure default subnet masks. If you are using non-standard masks, you must explicitly configure the mask, otherwise, it is not necessary.
In the following sample configuration, an IP address is assigned to VLAN 1, the inside interface.
ciscoasa(config-if)# interface vlan 1
ciscoasa(config-if)# ip address 192.168.106.1
In the following sample configuration, an interface VLAN 2, the outside interface is configured as a DHCP client. The use of the statement “setroute” tells the appliance to get its default route from the DHCP server.
ciscoasa(config-if)# interface vlan 2
ciscoasa(config-if)# ip address dhcp setroute
Configuring interfaces on 55×0 appliances
Notice on the screen capture from a Cisco ASA 5540 security appliance that the nameif command is used to name physical interfaces instead of VLAN interfaces.
![interface g01 configuration]()
switchport access
The switchport access command on the ASA 5505 security appliance assigns a physical interface to a logical (VLAN) interface. In the next example, the interface command is used to identify physical interfaces, assign them to switchports on the appliance, and enable them (turn them on). This command is not used on the ASA 55×0 appliances.
ciscoasa(config-if)# interface ethernet 0/0
ciscoasa(config-if)# switchport access vlan 2
ciscoasa(config-if)# no shutdown
ciscoasa(config-if)# interface ethernet 0/1
ciscoasa(config-if)# switchport access vlan 1
ciscoasa(config-if)# no shutdown
object network net-192.168.106
The object network net-192.168.106 statement creates an object called “net-192.168.106”. (You do not have to name the object “net-192.168.106”; that is a descriptive name, but you could just as easily name it “Juan”.) The network option states that this particular object will be based on IP addresses. The subnet 192.168.106.0 255.255.255.0 command states that net-192.168.106 will affect any IP address beginning with 192.168.106.
ciscoasa(config-if)#object network net-196.168.106
ciscoasa(config-network-object)#subnet 192.168.106.0 255.255.255.0
nat
The nat statement, as shown below, tells the firewall to allow all traffic flowing from the inside to the outside interface to use whatever address is dynamically (DHCP) configured on the outside interface.
ciscoasa(config)#nat (inside,outside) dynamic interface
route
The route command, in its most basic form, assigns a default route for traffic, typically to an ISP’s router. It can also be used in conjunction with access-lists to send specific types of traffic to specific hosts on specific subnets.
In this sample configuration, the route command is used to configure a default route to the ISP’s router at 12.3.4.6. The two zeroes before the ISP’s router address are shorthand for an IP address of 0.0.0.0 and a mask of 0.0.0.0. The statement outside identifies the interface through which traffic will flow to reach the default route.
ciscoasa(config-if)# route outside 0 0 12.3.4.6
In place of the manual default route configuration, as mentioned previously, you could instead configure your outside interface as a DHCP client and include the “setroute” statement to obtain the default route from the ISP’s DHCP server.
The above commands create a very basic firewall. A sophisticated firewall such as the Cisco ASA Security Appliance is capable of much greater functionality than what is shown here. These commands, however, will provide a solid foundation for configuring additional services on your appliance.
Other commands you might use include hostname to identify the firewall, telnet or SSH to allow remote administration, DHCPD commands to allow the firewall to assign IP addresses to inside hosts, and static route and access-list commands to allow internal hosts such as DMZ Web servers or DMZ mail servers to be accessible to Internet hosts. Of course, there are many more advanced commands that are explained in other how-to guides and in the book The Accidental Administrator: Cisco ASA Security Appliance: A Step-by-Step Configuration Guide.
Sample Base Configuration #1 (Static IP Address on Outside Interface)
ciscoasa(config)# interface vlan1
ciscoasa(config-if)# nameif inside
INFO: Security level for “inside” set to 100 by default.
ciscoasa(config-if)# interface vlan2
ciscoasa(config-if)# nameif outside
INFO: Security level for “outside” set to 0 by default.
ciscoasa(config-if)# interface ethernet 0/0
ciscoasa(config-if)# switchport access vlan 2
ciscoasa(config-if)# no shutdown
ciscoasa(config-if)# interface ethernet 0/1
ciscoasa(config-if)# switchport access vlan 1
ciscoasa(config-if)# no shutdown
ciscoasa(config-if)# interface vlan 2
ciscoasa(config-if)# ip address 12.3.4.5 255.255.255.0
ciscoasa(config-if)# interface vlan 1
ciscoasa(config-if)# ip address 192.168.106.1
ciscoasa(config-if)# route outside 0 0 12.3.4.6
ciscoasa(config-if)#object network net-192.168.106
ciscoasa(config-network-object)#subnet 192.168.106.0 255.255.255.0
ciscoasa(config)#nat (inside,outside) dynamic interface
ciscoasa(config)#exit
Note in the above configuration that the outside interface address and default route are configured manually. If your appliance’s outside interface is connected to a network with a DHCP server, such as an ISP, you could configured interface VLAN2 as a DHCP client with the command “ip address dhcp setroute”. The use of the “setroute” statement also eliminates the need for the manual default route configuration (route outside 0 0 12.3.4.6).
Sample Base Configuration #2 (DHCP-assigned IP Address on Outside Interface)
ciscoasa(config)# interface vlan1
ciscoasa(config-if)# nameif inside
INFO: Security level for “inside” set to 100 by default.
ciscoasa(config-if)# interface vlan2
ciscoasa(config-if)# nameif outside
INFO: Security level for “outside” set to 0 by default.
ciscoasa(config-if)# interface ethernet 0/0
ciscoasa(config-if)# switchport access vlan 2
ciscoasa(config-if)# no shutdown
ciscoasa(config-if)# interface ethernet 0/1
ciscoasa(config-if)# switchport access vlan 1
ciscoasa(config-if)# no shutdown
ciscoasa(config-if)# interface vlan 2
ciscoasa(config-if)# ip address dhcp setroute
ciscoasa(config-if)# interface vlan 1
ciscoasa(config-if)# ip address 192.168.106.1
ciscoasa(config-if)#object network net-192.168.106
ciscoasa(config-network-object)#subnet 192.168.106.0 255.255.255.0
ciscoasa(config)#nat (inside,outside) dynamic interface
ciscoasa(config)#exit
![]()
![]()


















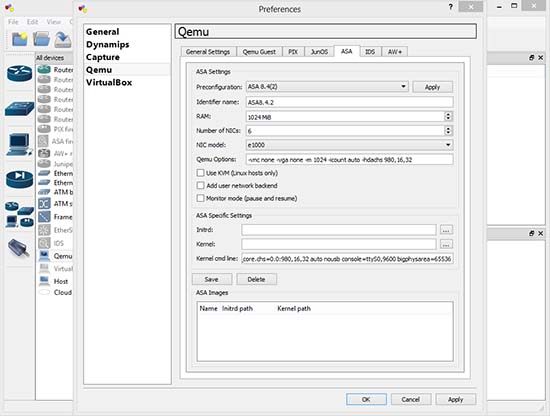
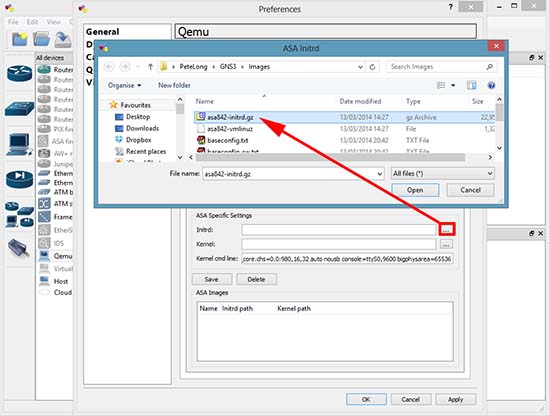
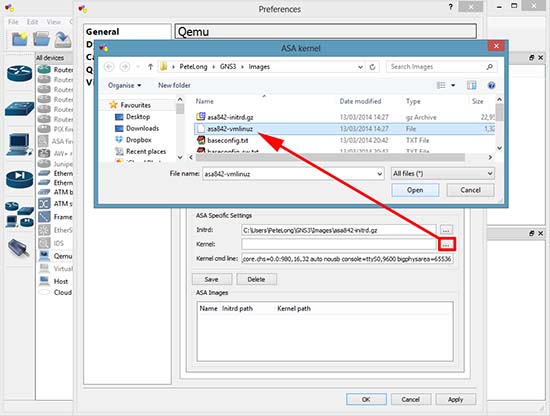
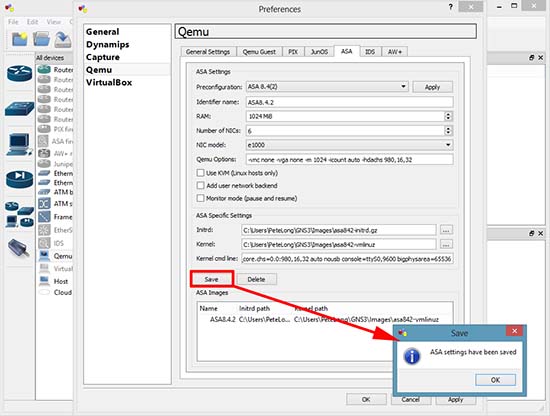










 As I have configured my system & vm to make use of ram at 90 % . At 90 % there was no swapping
As I have configured my system & vm to make use of ram at 90 % . At 90 % there was no swapping